The critical chain technique was developed by Dr. Eliyahu Goldratt in his 1997 business novel, Critical Chain1.
The method builds on the principles of critical path analysis and resource limited scheduling to identify chains of activities that are constrained by both dependencies and resource availability. Importantly, the technique then goes on to take aspects of human nature into account.
The concept of ‘safety’ relates to the fact that many people will provide activity duration estimates that are based on previous bad experiences. They naturally include contingency so that they are confident that they can definitely complete the activity in the time estimated (even when, as they expect, things don’t go as efficiently as they could).
If a project schedule has so much built-in safety, it would be reasonable to expect that it would be met every time but Goldratt identified three reasons why this doesn’t happen.
-
The student syndrome: because people know there is built in safety, they wait until the last minute to start the work.
-
Multitasking: when people have multiple activities on multiple projects to perform, they attempt to work on them simultaneously and this creates inefficiencies.
-
Dependencies between activities: delays accumulate faster than advances, i.e. if an activity finishes late then the following activity will be delayed but if an activity finishes early the following activity is less likely to be started early.
Many people add Parkinson’s Law to these three, i.e. the work will fill the time available to do it.
In simple terms, critical chain addresses these issues by applying the following principles:
-
Estimate activity durations to represent a 50/50 chance of completion. Collect the additional safety time into ‘buffers’.
-
Identify the critical chain, which represents the combination of dependencies and resources that are the principle constraint on the project’s duration.
-
Calculate the safety times on the critical chain to create a ‘project buffer’ at the end of the critical chain. Calculate the safety times for non-critical chains and create ‘feeder buffers’ at the end of each chain.
Project control then focuses on the management of the buffers rather than the individual activities.
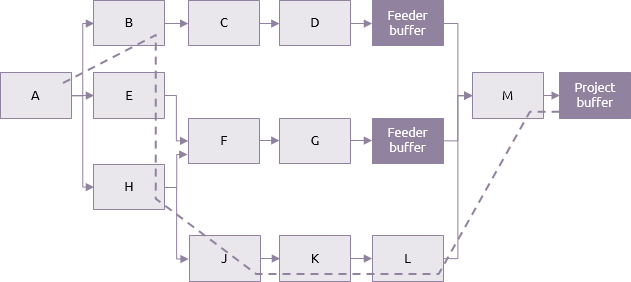
In the network above, the dotted line represents the critical chain. Based on a combination of the activity dependencies and resource requirements, this is the longest path that controls the project duration. The safety elements of the activities on this chain are used to calculate the project buffer. Other, non-critical chains are given feeder buffers.
- Goldratt, E M (1997), Critical Chain, North River Press, Great Barrington, MA.





